On the Hacker101 CTF, there’s a challenge that forces you to perform a padding oracle attack to win.
First, I looked at the Wikipedia, then the original paper, then some Youtube videos.
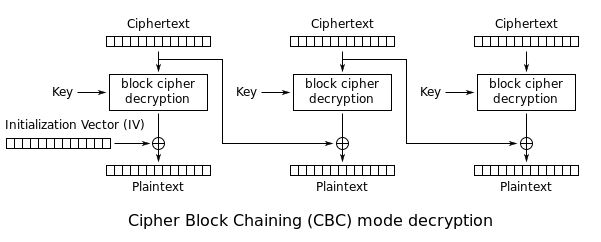
Then I wrote a quick perl script. It was slow. Partly because it was single-threaded, and partly because every brute-force attempt went over HTTP. Worse: it only worked sometimes, because I had an off-by-one error in a loop.
It took 20 minutes to find out it failed or succeeded.
I rewrote the script in Go. This time I understood the attack much better, and writing multithreaded code is easier in Go. Also, Perl has a really weird API for twiddling bits.
The Go rewrite worked great and I finally beat the challenge:

I wanted to visualize the attack and started rewriting it in Javascript with my friend Joe.
Visualizing it felt important to me. I wish I had something like that when I started this challenge.
I don’t normally do much with Javascript, so I tried and learned a lot of new things:
- used Webpack for the first time
- set up eslint with AirBnb’s rules
- Got prettier config working
- Lots of vimrc editing and plugins
I used the SubtleCrypto API to do the encryption. Did you know that you can’t use the SubtleCrypto API in chrome over a non-SSL connection? That was a fun one to figure out!
Later, I tried to make the same visualization with SVGs and learned a lot. That part isn’t done yet — SVG has a lot more dark corners than I anticipated.
You can try it out by checking out my post here: Visualizing the Padding Oracle Attack.